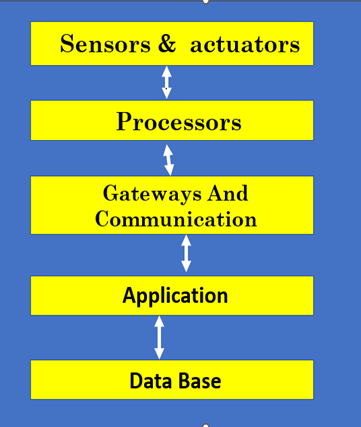
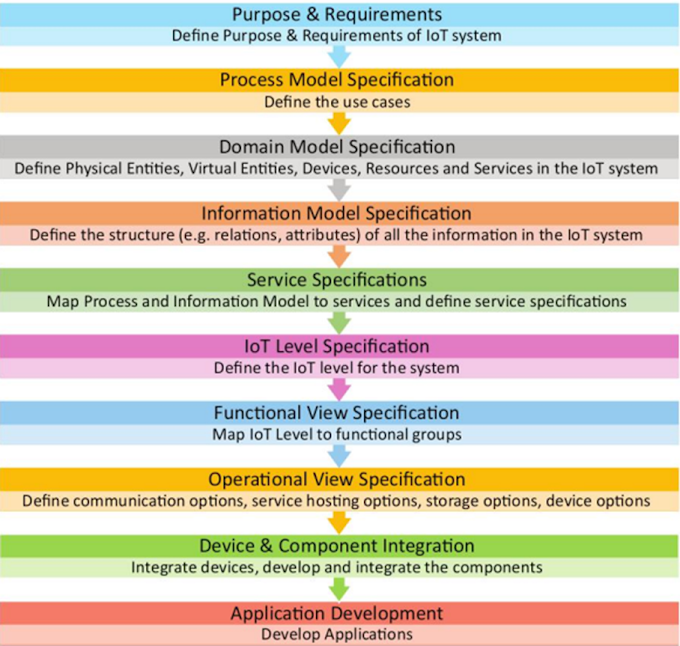
APPLICATION-LEVEL SECURITY IN THE CLOUD
· Application-level
security in the cloud focuses on protecting applications and their associated
data from various threats and vulnerabilities.
Some key
components and practices of application-level security in the cloud:
1. Secure Software Development Lifecycle (SDLC)
- Secure Coding
Practices:
Implementing secure coding standards to prevent common vulnerabilities such as
SQL injection, cross-site scripting (XSS), and buffer overflows.
2. Authentication and Authorization
- Strong
Authentication:
Implementing strong authentication mechanisms, such as multi-factor
authentication (MFA), to verify the identity of users.
3. Encryption
- Data Encryption: Encrypting data
at rest and in transit to protect it from unauthorized access. This includes
using HTTPS/TLS for secure communication and encryption protocols like AES for
data storage.
4. API Security
- API Gateway: Using an API
gateway to manage and secure API traffic, enforce policies, and monitor usage.
5. Input Validation and Sanitization
- Input
Validation:
Ensuring that all user inputs are validated to prevent malicious data from
entering the application.
6. Logging and Monitoring
- Activity
Logging:
Logging all significant actions and events within the application to provide an
audit trail.
7. Patch Management
- Regular Updates: Keeping all
components of the application, including third-party libraries and
dependencies, up to date with the latest security patches.
8. Security Testing
- Penetration
Testing:
Conducting regular penetration tests to identify and exploit vulnerabilities in
the application.
9. Configuration Management
- Secure Defaults: Ensuring that
applications are deployed with secure default settings.
10. Incident Response
- Response Plan: Developing and
maintaining an incident response plan to handle security incidents effectively.

0 Comments