ANSWERS OF MODEL QUESTIONS OF IOT- 2024
:
-
1. What is the
Internet of Things (IoT) and how does it differ from traditional
internet-connected devices?
The Internet of Things (IoT) refers to a
network of interconnected devices embedded with sensors, software, and other
technologies, enabling them to collect and exchange data with other devices and
systems over the Internet. Unlike traditional internet-connected devices, which
primarily focus on human interaction, IoT devices communicate with each other
autonomously, facilitating machine-to-machine (M2M) communication. IoT devices
are often designed to gather data from their surroundings, process it locally
or in the cloud, and respond accordingly without human intervention.
2. How has IoT
transformed various industries and everyday life?
IoT has revolutionized various industries
and everyday life in several ways:
- In healthcare, IoT devices enable remote
patient monitoring, personalized treatment, and efficient management of medical
resources.
- In agriculture, IoT-based solutions
improve crop monitoring, irrigation management, and livestock tracking, leading
to higher yields and reduced resource wastage.
- In manufacturing, IoT facilitates
predictive maintenance, real-time monitoring of equipment, and optimization of
supply chain operations, enhancing efficiency and reducing downtime.
- In smart homes, IoT devices automate
household tasks, enhance security through surveillance systems, and optimize
energy consumption, leading to increased comfort and convenience.
3. Define IoT and
enumerate its key characteristics.
IoT can be defined as a network of
interconnected devices embedded with sensors, software, and other technologies,
enabling them to collect and exchange data over the Internet. Key
characteristics of IoT include:
- Connectivity: IoT devices are connected to
the internet or other devices, enabling seamless communication and data
exchange.
- Sensing and Actuation: IoT devices are
equipped with sensors to collect data from the physical world and actuators to
perform actions based on that data.
- Data Processing: IoT devices process data
locally or in the cloud to derive insights and make informed decisions.
- Automation: IoT enables automation of
various tasks and processes, reducing manual intervention and improving
efficiency.
- Scalability: IoT systems can scale to
accommodate a large number of devices and data sources, facilitating widespread
adoption and deployment.
4. How does IoT
leverage sensor data and connectivity to enhance functionality?
IoT leverages sensor data and connectivity
in the following ways to enhance functionality:
- Sensor Data Collection: IoT devices
collect data from their surroundings using various sensors, such as
temperature, humidity, motion, and GPS.
- Data Transmission: IoT devices transmit
the collected data over the internet or local networks to centralized servers
or other devices for further processing and analysis.
- Real-time Monitoring: IoT enables
real-time monitoring of assets, environments, and processes, allowing for
timely detection of anomalies or events.
- Data Analysis: IoT platforms analyze the
collected data to derive insights, identify patterns, and make predictions,
enabling informed decision-making and optimization of operations.
- Remote Control: IoT devices can receive
commands remotely and actuate accordingly, allowing for remote monitoring and
control of devices and systems.
5. Describe the
typical architecture of an IoT system, including the roles of edge devices,
gateways, cloud platforms, and applications.
The typical architecture of an IoT system
consists of the following components:
- Edge Devices: These are the IoT devices
deployed at the network edge, equipped with sensors and actuators to collect
and process data locally.
- Gateways: Gateways serve as intermediaries
between edge devices and the cloud, aggregating and preprocessing data before
transmitting it to the cloud platform.
- Cloud Platform: The cloud platform
receives and stores data from edge devices, performs data analysis and
processing, and provides services such as data visualization, predictive
analytics, and device management.
- Applications: Applications interact with
the cloud platform to access and analyze IoT data, monitor device status, and
control devices remotely. These applications may include dashboards, mobile
apps, and web interfaces for end users and administrators.
6. What are the
challenges associated with IoT architecture scalability and interoperability?
Challenges associated with IoT architecture
scalability and interoperability include:
- Scalability: Accommodating a large number
of devices, managing increasing data volumes, and ensuring seamless integration
with existing systems.
- Interoperability: Ensuring compatibility
and communication among diverse devices, protocols, and platforms from
different manufacturers.
- Standardization: Lack of standardized
protocols and frameworks leading to vendor lock-in, complexity in system
integration, and reduced flexibility.
- Security and Privacy: Protecting sensitive
data, securing communication channels, and preventing unauthorized access in a
scalable and interoperable manner.
7. Explain the
logical design considerations for developing an IoT solution, such as data
collection, processing, and analysis.
Logical design considerations for developing
an IoT solution include:
- Data Collection: Identifying relevant data
sources, selecting appropriate sensors, and defining data collection mechanisms
and protocols.
- Data Processing: Determining data
processing requirements, such as real-time or batch processing, edge computing
versus cloud computing, and selecting suitable algorithms for data analysis and
interpretation.
- Data Analysis: Establishing analytics
pipelines, defining data models and schemas, and implementing visualization
techniques to extract actionable insights from the collected data.
8. How can
security and privacy be integrated into the logical design of IoT systems?
Security and privacy can be integrated into
the logical design of IoT systems through:
- Authentication and Authorization:
Implementing strong authentication mechanisms, role-based access control, and
secure communication protocols to prevent unauthorized access.
- Encryption: Encrypting data at rest and in
transit to safeguard sensitive information from unauthorized disclosure or
tampering.
- Secure Protocols: Using secure
communication protocols such as HTTPS, MQTT with TLS, and CoAP with DTLS to
protect data integrity and confidentiality.
- Privacy by Design: Incorporating
privacy-enhancing features such as data anonymization, pseudonymization, and
consent management into the system architecture from the outset.
9. Discuss common
communication protocols used in IoT ecosystems, such as MQTT, CoAP, and HTTP.
Common communication protocols used in IoT
ecosystems include:
- MQTT (Message Queuing Telemetry
Transport): Lightweight publish-subscribe messaging protocol designed for
resource-constrained devices, enabling efficient, low-latency communication
with minimal overhead.
- CoAP (Constrained Application Protocol):
Designed for constrained networks and devices, CoAP provides a RESTful
communication model over UDP, supporting resource discovery, caching, and
observe patterns.
- HTTP (Hypertext Transfer Protocol): Widely
used for web communication, HTTP can be adapted for IoT applications, although
it may have higher overhead compared to MQTT and CoAP, making it less suitable
for resource-constrained environments.
10. How do these
protocols address the requirements of IoT applications, such as low power
consumption and reliability?
These protocols address the requirements of
IoT applications such as low power consumption and reliability through:
- Lightweight Messaging: MQTT and CoAP are
designed to minimize message size and protocol overhead, reducing energy
consumption and bandwidth usage, particularly in resource-constrained
environments.
- QoS Levels: MQTT supports Quality of
Service (QoS) levels to ensure message delivery reliability, with options for
at-most-once, at-least-once, and exactly-once delivery semantics.
- UDP-based Communication: CoAP operates
over UDP, which offers low-latency communication and reduced overhead compared
to TCP, making it suitable for unreliable networks and low-power devices.
11. Enumerate
different types of IoT devices and their respective applications in various
domains, such as wearables, smart home devices, and industrial sensors.
Different types of IoT devices include:
- Wearables: Smartwatches, fitness
trackers, and healthcare devices for monitoring vital signs, activity levels,
and personal wellness.
- Smart Home Devices: Thermostats, security
cameras, lighting controls, and smart appliances for home automation, energy
management, and security.
- Industrial Sensors: Temperature sensors,
pressure sensors, flow meters, and RFID tags for monitoring and controlling
manufacturing processes, supply chain logistics, and asset tracking.
12. What are the
key considerations in designing IoT devices for specific use cases?
Key considerations in designing IoT devices
for specific use cases include:
- Hardware Selection: Choosing appropriate
sensors, actuators, microcontrollers, and communication modules based on the
application requirements and environmental conditions.
- Power Management: Optimizing power
consumption through low-power hardware components, energy-efficient
communication protocols, and power-saving sleep modes to extend battery life.
- Data Security: Implementing secure
authentication, encryption, and access control mechanisms to protect sensitive
data and prevent unauthorized access or tampering.
- Connectivity: Select reliable
communication protocols and network technologies such as Wi-Fi, Bluetooth,
Zigbee, or LoRaWAN based on range, bandwidth, and power requirements.
13. Define M2M
communication and compare it with IoT in terms of scope, connectivity, and
applications.
M2M (Machine-to-Machine) communication
refers to direct communication between devices without human intervention,
typically over wired or wireless networks.
- Scope: M2M communication typically
involves a predefined set of devices exchanging data for specific purposes,
such as remote monitoring, control, or automation of industrial equipment or
infrastructure.
- Connectivity: M2M communication often
relies on point-to-point connections or dedicated networks optimized for
machine communication, such as SCADA (Supervisory Control and Data Acquisition)
systems or industrial control networks.
- Applications: M2M communication is
commonly used in industrial automation, smart grid management, fleet tracking,
and asset monitoring applications, where devices communicate to optimize
operations, improve efficiency, and reduce downtime.
IoT (Internet of Things), on the other
hand, encompasses a broader concept of interconnected devices, sensors, and
systems that communicate over the Internet, enabling diverse applications
beyond industrial automation.
- Scope: IoT encompasses a wider range of
devices, including consumer electronics, wearables, smart home devices, and
environmental sensors, enabling applications in healthcare, agriculture,
transportation, and smart cities.
- Connectivity: IoT devices typically
leverage internet connectivity and standard communication protocols, enabling
interoperability, scalability, and integration with cloud-based services and
applications.
- Applications: IoT applications span
various domains, including healthcare monitoring, home automation, precision
agriculture, smart transportation, and environmental monitoring, with a focus
on enhancing convenience, efficiency, and sustainability.
14. Explain how
SDN can enhance network management and efficiency in IoT deployments.
SDN (Software-Defined Networking) enhances
network management and efficiency in IoT deployments by:
- Centralized Control: SDN decouples the
control plane from the data plane, allowing centralized control and
programmability of network devices through a software controller.
- Dynamic Resource Allocation: SDN enables
dynamic allocation of network resources based on real-time traffic patterns,
device requirements, and application demands, optimizing network performance
and scalability.
- Policy-Based Management: SDN allows
administrators to define and enforce policies for traffic routing, QoS (Quality
of Service), security, and access control across heterogeneous IoT devices and
networks, ensuring consistent management and compliance.
- Network Virtualization: SDN facilitates
network virtualization and segmentation, enabling multi-tenancy, isolation, and
logical network abstraction to support diverse IoT applications and services.
- Automation and Orchestration: SDN
automates network provisioning, configuration, and orchestration tasks,
- Integration with
IoT Platforms: SDN integrates with IoT platforms and cloud services, enabling
seamless connectivity, data exchange, and orchestration of IoT devices and
applications.
- Traffic Engineering: SDN enables
intelligent traffic engineering and load balancing to optimize network
performance, reduce congestion, and ensure efficient data delivery in IoT
deployments.
- Security Enforcement: SDN allows for
dynamic security policies and enforcement mechanisms to detect and mitigate
cyber threats, anomalies, and unauthorized access in IoT networks, enhancing
overall security posture.
- Flexibility and Scalability: SDN provides
flexibility and scalability to adapt to changing IoT requirements, scale
network infrastructure, and accommodate new devices, services, and applications
seamlessly.
15. Discuss the
role of NFV in virtualizing network functions to support dynamic IoT
environments.
NFV (Network Function Virtualization) plays
a crucial role in virtualizing network functions to support dynamic IoT
environments by:
- Decoupling Hardware and Software: NFV
decouples network functions from proprietary hardware appliances, enabling them
to run as software instances on commodity hardware or virtual machines.
- Virtual Network Function (VNF) Deployment:
NFV allows for the deployment and instantiation of virtualized network
functions, such as firewalls, load balancers, and gateways, on-demand and at
scale, based on application requirements.
- Service Chaining: NFV enables the creation
of service chains by chaining together multiple virtualized network functions
dynamically to implement complex network services and policies tailored to IoT
use cases.
- Resource Optimization: NFV optimizes
resource utilization by dynamically allocating and scaling virtualized network
functions based on workload demands, traffic patterns, and service level
agreements (SLAs) in IoT environments.
- Rapid Service Deployment: NFV accelerates
service deployment and innovation by abstracting network functions from the underlying hardware, enabling agile service provisioning, testing, and rollout
to meet evolving IoT requirements.
16. What are the
benefits and challenges of adopting SDN and NFV in IoT infrastructures?
The benefits of adopting SDN and NFV in IoT
infrastructures include:
- Enhanced Flexibility: SDN and NFV provide
flexibility to adapt and scale network infrastructure, services, and
applications dynamically to meet evolving IoT requirements and business needs.
- Improved Efficiency: SDN and NFV optimize
resource utilization, automate network operations, and enable rapid service
deployment, reducing operational costs and time-to-market for IoT solutions.
- Enhanced Security: SDN and NFV enable
dynamic security policies, isolation, and enforcement mechanisms to detect,
mitigate, and respond to cyber threats, vulnerabilities, and attacks in IoT
networks.
- Accelerated Innovation: SDN and NFV foster
innovation by enabling programmable, open, and standards-based network
architectures, encouraging collaboration, interoperability, and ecosystem
growth in the IoT space.
Challenges of adopting SDN and NFV in IoT
infrastructures include:
- Complexity: SDN and NFV introduce
complexity in network design, management, and integration, requiring
specialized skills, tools, and expertise to deploy and operate effectively in
IoT environments.
- Interoperability: SDN and NFV solutions
may face interoperability challenges with legacy systems, proprietary
protocols, and heterogeneous IoT devices, hindering seamless integration and
migration.
- Scalability: SDN and NFV scalability may
be limited by hardware resources, performance bottlenecks, and orchestration
overhead, impacting the ability to scale network functions and services
dynamically to support large-scale IoT deployments.
- Security Risks: SDN and NFV introduce new
security risks, such as virtualization vulnerabilities, orchestration attacks,
and control plane exploits, requiring robust security measures and best
practices to mitigate risks and protect IoT assets.
- Standardization: SDN and NFV standards and
frameworks may still be evolving, leading to interoperability issues, vendor
lock-in, and fragmentation in the IoT ecosystem, necessitating industry
collaboration and standardization efforts to address gaps and ensure
compatibility.
----------------------------------------------------------------------
17. Why is
effective system management crucial in IoT deployments?
Effective system management is crucial in
IoT deployments for the following reasons:
- Scale: IoT deployments often involve a
large number of interconnected devices spread across diverse environments.
Effective management ensures seamless coordination, monitoring, and control of
these devices.
- Reliability: IoT systems must operate
reliably to support critical functions in industries such as healthcare,
manufacturing, and transportation. System management helps detect and mitigate
issues to maintain high reliability.
- Security: IoT devices are susceptible to
cyber threats and vulnerabilities. System management involves implementing
security measures such as authentication, encryption, and access control to
protect IoT assets and data.
- Optimization: System management enables
optimization of IoT resources, performance, and energy consumption, leading to
improved efficiency, cost savings, and sustainability.
- Compliance: IoT deployments may be subject
to regulatory requirements and industry standards. System management helps
ensure compliance with relevant regulations and standards, reducing legal and
financial risks.
18. What are the
main challenges associated with managing large-scale IoT systems?
The main challenges associated with managing
large-scale IoT systems include:
- Device Diversity: Managing a diverse range
of IoT devices with varying capabilities, protocols, and firmware versions can
be complex and resource-intensive.
- Data Volume: Large-scale IoT deployments
generate massive volumes of data from sensors, devices, and applications.
Managing and processing this data efficiently is a significant challenge.
- Connectivity: Ensuring reliable
connectivity for a large number of devices, especially in remote or challenging
environments, poses challenges in terms of network coverage, reliability, and
bandwidth.
- Security: Securing large-scale IoT systems
against cyber threats, such as unauthorized access, data breaches, and malware
attacks, requires robust security measures and constant vigilance.
- Scalability: IoT systems must scale
seamlessly to accommodate growing numbers of devices, users, and data sources
without compromising performance, reliability, or manageability.
- Interoperability: Achieving
interoperability among heterogeneous IoT devices, platforms, and protocols is
crucial for seamless communication, data exchange, and integration but can be
challenging due to proprietary standards and vendor lock-in.
19. What is SNMP,
and how is it used for managing networked devices in IoT environments?
SNMP (Simple Network Management Protocol) is
a widely used protocol for managing networked devices in IoT environments. It
allows network administrators to monitor and control devices such as routers,
switches, servers, and IoT gateways remotely. SNMP operates based on a
manager-agent model, where SNMP managers (centralized systems) communicate with
SNMP agents (embedded in devices) to retrieve and modify device parameters and
status information.
20. Explain the
key components of SNMP, including managers, agents, and MIBs (Management
Information Bases).
- SNMP Managers: SNMP managers are
centralized systems responsible for monitoring and controlling networked
devices. They send SNMP requests to agents and receive SNMP traps and
notifications. Managers use SNMP protocols to query device information and
perform management tasks.
- SNMP Agents: SNMP agents are software
modules embedded in networked devices. They collect and store device
information in Management Information Bases (MIBs) and respond to SNMP requests
from managers. Agents also generate SNMP traps to notify managers of
significant events or alarms.
- Management Information Bases (MIBs): MIBs
are hierarchical databases that store structured information about managed
devices. They define the structure and semantics of managed objects, including
device parameters, status variables, and performance metrics. MIBs use a
standardized notation called SNMP Object Identifiers (OIDs) to uniquely
identify managed objects and facilitate communication between managers and
agents.
21. Discuss the
essential requirements for managing IoT systems, considering aspects such as
scalability, security, and interoperability.
Essential requirements for managing IoT
systems include:
- Scalability: IoT systems should scale
seamlessly to accommodate growing numbers of devices, users, and data sources
without compromising performance or manageability.
- Security: IoT systems must implement
robust security measures to protect against cyber threats, unauthorized access,
data breaches, and malware attacks. This includes encryption, authentication,
access control, and secure communication protocols.
- Interoperability: IoT systems should
ensure interoperability among heterogeneous devices, platforms, and protocols
to facilitate seamless communication, data exchange, and integration across the
ecosystem.
- Remote Management: IoT systems should
support remote management and configuration of devices, applications, and
services to enable centralized monitoring, control, and troubleshooting.
- Data Management: IoT systems should manage
and process large volumes of data efficiently, including data collection,
storage, analysis, and visualization, to derive actionable insights and support
decision-making.
- Over-the-Air Updates: IoT systems should
support over-the-air (OTA) updates to remotely deploy firmware updates,
security patches, and software upgrades to devices, ensuring they remain
up-to-date and secure.
- Fault Tolerance: IoT systems should
incorporate fault-tolerant mechanisms to detect and recover from failures,
minimize downtime, and maintain high availability and reliability of services.
- Compliance and Standards: IoT systems
should adhere to regulatory requirements, industry standards, and best
practices to ensure compliance, interoperability, and trustworthiness, reducing
legal and financial risks.
22. How do these
requirements differ from traditional network management approaches?
The requirements for managing IoT systems
differ from traditional network management approaches in several ways:
- Scale: IoT systems typically involve a
much larger number of devices distributed across diverse environments compared
to traditional networks. Managing this scale requires new approaches to
scalability, resource allocation, and performance optimization.
- Heterogeneity: IoT devices come in various
forms, with different capabilities, protocols, and operating environments.
Managing heterogeneous IoT ecosystems requires interoperability standards,
protocol translation, and device management solutions that may not be necessary
in traditional networks.
- Data Volume and Variety: IoT systems
generate massive volumes of data from sensors, devices, and applications, often
in diverse formats and structures. Managing and analyzing this data require
advanced techniques for data acquisition, processing, and storage beyond what
is needed in traditional network management.
- Security and Privacy: IoT systems face
unique security and privacy challenges due to the distributed nature of
devices, the proliferation of attack vectors, and the sensitivity of the data
involved. Managing security in IoT requires comprehensive solutions for
authentication, encryption, access control, and threat detection that go beyond
traditional network security measures.
23. Describe a
methodology for designing IoT platforms, considering factors like data
acquisition, processing, storage, and application interfaces.
A methodology for designing IoT platforms
typically involves the following steps:
- Requirement Analysis: Identify the
specific requirements and use cases for the IoT platform, including data types,
volume, velocity, and variety, as well as user requirements for applications
and interfaces.
- Data Acquisition: Determine the sources of
data to be collected, including sensors, devices, and external systems, and
define protocols and mechanisms for data acquisition, such as MQTT, CoAP, or
REST APIs.
- Data Processing: Design data processing
pipelines and workflows to ingest, filter, aggregate, and analyze the collected
data, leveraging technologies such as stream processing, batch processing, and
machine learning algorithms.
- Storage and Management: Select appropriate
data storage solutions based on requirements for scalability, performance, and
data retention, such as databases, data lakes, or distributed file systems, and
define data management policies for data lifecycle management, access control,
and compliance.
- Application Interfaces: Design application
interfaces, including APIs, SDKs, and user interfaces, to enable integration
with external systems, development of custom applications, and interaction with
end users, ensuring usability, scalability, and security.
24. What are the
key considerations in selecting hardware and software components for an IoT
platform?
Key considerations in selecting hardware and
software components for an IoT platform include:
- Hardware: Consider factors such as
processing power, memory, connectivity options (e.g., Wi-Fi, Bluetooth,
cellular), power consumption, ruggedness, and scalability when selecting IoT
devices and gateways.
- Software: Evaluate software platforms,
frameworks, and tools for data acquisition, processing, storage, and
application development, considering factors such as compatibility,
scalability, performance, security, and community support.
- Interoperability: Choose hardware and
software components that support interoperability standards and protocols to
ensure compatibility and seamless integration with existing systems and future
expansion.
- Security: Select hardware and software
solutions with built-in security features, such as secure boot, encryption,
authentication, and over-the-air updates, to protect IoT devices, data, and
communications from cyber threats.
- Flexibility and Customization: Look for
hardware and software components that offer flexibility and customization
options to meet specific requirements and adapt to evolving use cases, business
needs, and technology trends.
- Cost-effectiveness: Consider the total
cost of ownership (TCO), including upfront costs, maintenance expenses, and
lifecycle costs, when selecting hardware and software components to ensure
cost-effectiveness and ROI.
25. Explain the
logical design process for an IoT system, including data flow modeling,
component identification, and communication protocols.
The logical design process for an IoT system
typically involves the following steps:
- Data Flow Modeling: Identify the flow of
data within the IoT system, including data sources, data processing steps, data
storage locations, and data consumption points. Create data flow diagrams or
models to visualize data movement and transformations.
- Component Identification: Identify the key
components of the IoT system, including edge devices, gateways, cloud
platforms, applications, and interfaces. Define the roles, responsibilities,
and interactions of each component in the system architecture.
- Communication Protocols: Select
communication protocols and standards for device-to-device communication,
device-to-cloud communication, and inter-component communication, considering
factors such as bandwidth, latency, reliability, and security requirements.
Common IoT communication protocols include MQTT, CoAP, HTTP, and WebSocket.
- Security Considerations: Incorporate
security measures and best practices into the logical design of the IoT system,
including authentication, encryption, access control, and secure communication
protocols, to protect against cyber threats and ensure data confidentiality,
integrity, and availability.
26. How do you
ensure flexibility and adaptability in the logical design of IoT systems to
accommodate evolving requirements?
To ensure flexibility and adaptability in
the logical design of IoT systems, consider the following approaches:
- Modular Design: Adopt a modular
architecture that allows components to be added, removed, or replaced easily
without affecting the overall system functionality. Use standardized interfaces
and protocols to facilitate interoperability and integration with third-party
systems.
- Scalable Infrastructure: Design the IoT
system with scalability in mind, using cloud-based services, distributed
architectures, and elastic resources that can scale dynamically to accommodate
changing requirements, workload fluctuations, and growth in data volume or user
base.
- Open Standards: Embrace open standards,
protocols, and APIs to enable flexibility and interoperability, avoiding vendor
lock-in and ensuring compatibility with a wide range of devices, platforms, and
applications.
- Future-proofing: Anticipate future
requirements, trends, and advancements in technology when designing the IoT
system, incorporating features such as over-the-air updates, firmware
upgradeability, and backward compatibility to adapt to evolving standards,
regulations, and market demands.
- Agile Development: Adopt agile
methodologies and iterative development practices to continuously improve and
refine the IoT system based on user feedback, performance metrics, and changing
business needs. Iterate quickly, experiment with new ideas and pivot as
necessary to stay agile and responsive to changes in the IoT landscape.
27. Discuss the
importance of security mechanisms in IoT system management and identify common
security threats faced by IoT deployments.
Security mechanisms are crucial in IoT
system management to safeguard against various security threats that can
compromise the integrity, confidentiality, and availability of data and
devices. Common security threats faced by IoT deployments include:
- Unauthorized Access: Hackers may gain
unauthorized access to IoT devices, networks, or cloud platforms, leading to
data breaches, device hijacking, and unauthorized control.
- Data Breaches: Sensitive data collected by
IoT devices, such as personal information or industrial data, may be exposed to
unauthorized parties through hacking, interception, or data leakage.
- Denial of Service (DoS) Attacks: Attackers
may overwhelm IoT networks or cloud services with excessive traffic or
malicious requests, causing disruptions, downtime, or service degradation.
- Malware and Botnets: IoT devices may
become infected with malware or recruited into botnets, allowing attackers to
launch coordinated attacks, propagate malware, or steal data.
- Privacy Violations: IoT deployments may
raise privacy concerns due to the collection, storage, and analysis of personal
or sensitive data without consent or proper safeguards.
28. How can
encryption, authentication, and access control be integrated into IoT
management frameworks?
Encryption, authentication, and access
control can be integrated into IoT management frameworks through the following
mechanisms:
- Encryption: Implement end-to-end
encryption of data in transit and at rest using strong cryptographic algorithms
(e.g., AES, RSA) to protect data confidentiality and integrity.
- Authentication: Require mutual
authentication between IoT devices and cloud platforms using digital
certificates, tokens, or biometric methods to verify the identity of both
parties and prevent unauthorized access.
- Access Control: Enforce fine-grained
access control policies based on user roles, privileges, and attributes to
restrict access to sensitive data and critical operations, preventing
unauthorized actions and privilege escalation.
29. How can IoT
management systems be integrated with existing IT infrastructure and enterprise
management platforms?
IoT management systems can be integrated
with existing IT infrastructure and enterprise management platforms through:
- APIs and Standards: Use standardized APIs
(e.g., RESTful APIs, MQTT) and protocols (e.g., SNMP, CoAP) to enable
interoperability and integration with existing systems, applications, and
management platforms.
- Middleware and Integration Platforms:
Deploy middleware solutions or integration platforms that provide connectors,
adapters, and APIs for seamless communication and data exchange between IoT
management systems and enterprise systems (e.g., ERP, CRM).
- Data Integration and ETL Tools: Employ
data integration and ETL (Extract, Transform, Load) tools to ingest, transform,
and synchronize IoT data with enterprise databases, data warehouses, and
analytics platforms.
- Identity and Access Management (IAM):
Integrate IoT management systems with IAM solutions to centralize user
authentication, authorization, and identity federation across IoT and
enterprise environments, ensuring consistent access control and security
policies.
30. What are the
challenges and best practices for ensuring seamless integration and
interoperability?
Challenges for ensuring seamless integration
and interoperability in IoT deployments include:
- Heterogeneous Ecosystem: IoT devices,
platforms, and protocols come from diverse vendors with varying standards and
specifications, leading to interoperability issues and integration challenges.
- Legacy Systems: Integration with existing
IT infrastructure, legacy systems, and enterprise applications may require
custom adapters, middleware, or data transformation layers to bridge the gap
between old and new technologies.
- Data Silos: Data silos and disparate data
formats across IoT devices, applications, and systems hinder data sharing,
analysis, and decision-making, requiring data integration and standardization
efforts.
- Security and Privacy: Integrating IoT
systems without compromising security and privacy requires robust
authentication, encryption, access control, and compliance with regulatory
requirements.
Best practices for ensuring seamless
integration and interoperability include:
- Adopting Open Standards: Embrace open
standards and protocols for device communication, data exchange, and
interoperability to ensure compatibility and flexibility across diverse IoT
ecosystems.
- API-First Approach: Design IoT solutions
with APIs as first-class citizens, enabling developers to access and integrate
IoT functionalities programmatically with ease.
- Modular Architecture: Design IoT systems
with modular components and loosely coupled architectures to facilitate
integration, scalability, and flexibility.
- Testing and Validation: Conduct thorough
testing and validation of integration points, data flows, and interoperability
scenarios across different devices, platforms, and environments to ensure
seamless operation.
- Collaboration and Partnerships:
Collaborate with industry partners, consortia, and standards bodies to address
interoperability challenges collectively and foster innovation in IoT
ecosystems.
31. Explain the
role of monitoring and analytics tools in IoT system management.
Monitoring and analytics tools play a
critical role in IoT system management by providing insights into the
performance, health, and behavior of IoT devices, networks, and applications.
These tools enable:
- Real-time Monitoring: Continuous
monitoring of device status, connectivity, and performance metrics to detect
anomalies, faults, or deviations from expected behavior.
- Fault Detection and Diagnosis: Automated
detection, analysis, and troubleshooting of network issues, device failures,
and performance bottlenecks to minimize downtime and service disruptions.
- Predictive Maintenance: Analysis of
historical data, patterns, and trends to predict equipment failures, schedule
preventive maintenance, and optimize asset utilization and lifecycle
management.
- Performance Optimization: Identification
of performance optimization opportunities, such as resource allocation, traffic
shaping, and workload balancing, to improve efficiency, reliability, and
scalability.
- Data-driven Insights: Generation of
actionable insights, reports, and dashboards to inform decision-making, improve
operational efficiency, and drive business value from IoT investments.
32. How can
real-time data analysis and predictive maintenance improve the efficiency and
reliability of IoT deployments?
Real-time data analysis and predictive
maintenance can improve the efficiency and reliability of IoT deployments by:
- Early Fault Detection: Analyzing real-time
data from IoT devices allows for the early detection of anomalies and potential
faults, enabling proactive measures to be taken to prevent system failures or
downtime.
- Predictive Maintenance: By analyzing
historical data and patterns, predictive maintenance models can forecast when
equipment is likely to fail or require maintenance. This allows maintenance to
be scheduled in advance, reducing unplanned downtime and extending the lifespan
of assets.
- Optimal Resource Allocation: Real-time
analysis of data can help optimize resource allocation by dynamically adjusting
parameters such as energy consumption, network bandwidth, or processing power
based on current demand and conditions.
- Enhanced Reliability: Predictive analytics
can identify potential points of failure or weak links in the IoT system,
allowing for preemptive action to strengthen these areas and improve overall
system reliability.
- Cost Savings: By reducing unplanned
downtime, minimizing equipment failures, and optimizing resource usage,
real-time data analysis and predictive maintenance can lead to significant cost
savings in terms of maintenance expenses, operational efficiency, and asset
utilization.
- Improved Customer Satisfaction: Ensuring
the reliability and availability of IoT services through proactive maintenance
and optimized performance enhances customer satisfaction by minimizing service
disruptions and meeting user expectations for reliability and responsiveness.
33. What are the essential components or building
blocks required for creating IoT devices?
Essential
components for creating IoT devices include:
- Sensors: To
collect data from the environment (e.g., temperature, humidity, motion).
- Actuators:
To perform actions based on input or commands received (e.g., motors,
switches).
-
Microcontrollers or Microprocessors: To process data, execute algorithms, and
control device behavior.
-
Communication Modules: To enable connectivity and communication with other
devices or networks (e.g., Wi-Fi, Bluetooth, LoRa, Zigbee).
- Power
Source: To provide the necessary energy to operate the device (e.g., batteries,
solar panels).
34. Discuss the role of sensors, actuators,
microcontrollers, and communication modules in IoT device architecture.
- Sensors:
Sensors detect changes in the environment and convert them into electrical
signals. They play a crucial role in gathering data for monitoring and analysis
in IoT systems.
- Actuators:
Actuators receive signals from the microcontroller and perform physical actions
based on these signals. They enable IoT devices to interact with the physical
world by controlling motors, switches, valves, and other mechanisms.
-
Microcontrollers: Microcontrollers serve as the brains of IoT devices,
processing data from sensors, making decisions based on programmed logic or
algorithms, and sending commands to actuators. They typically have integrated
processing, memory, and I/O capabilities.
-
Communication Modules: Communication modules enable IoT devices to connect to
networks and exchange data with other devices or systems. They support various
wireless or wired communication protocols, such as Wi-Fi, Bluetooth, cellular,
Ethernet, LoRa, Zigbee, or MQTT, depending on the application requirements and
environmental constraints.
35. What is Raspberry Pi, and how is it used as an IoT
device?
Raspberry Pi
is a series of small, affordable single-board computers developed by the
Raspberry Pi Foundation. It is widely used in IoT applications due to its low
cost, versatility, and ease of use. Raspberry Pi can function as an IoT device
by connecting sensors, actuators, and communication modules to its GPIO
(General Purpose Input/Output) pins and USB ports, and running IoT software to
collect data, process it, and communicate with other devices or cloud platforms.
36. Describe the hardware specifications and
capabilities of Raspberry Pi for IoT applications.
- CPU:
Raspberry Pi boards feature ARM-based processors with varying clock speeds and
cores (e.g., Raspberry Pi 4 has a quad-core Cortex-A72 CPU).
- Memory:
Raspberry Pi models come with different amounts of RAM (e.g., Raspberry Pi 4 is
available with 2GB, 4GB, or 8GB of RAM).
- Storage:
Raspberry Pi typically uses microSD cards for primary storage, but newer models
may also support USB or network-attached storage options.
-
Connectivity: Raspberry Pi boards offer built-in connectivity options such as
Wi-Fi, Bluetooth, Ethernet, and USB ports for connecting peripherals and
accessories.
- GPIO Pins:
Raspberry Pi boards include GPIO pins that allow for interfacing with external
sensors, actuators, and other hardware components.
- Operating
System: Raspberry Pi supports various operating systems, including Raspberry Pi
OS (formerly Raspbian), Ubuntu, and other Linux distributions, as well as
Windows 10 IoT Core.
37. Provide examples of IoT projects or applications
implemented using Raspberry Pi.
Examples of
IoT projects or applications implemented using Raspberry Pi include:
- Home
Automation Systems: Controlling lights, thermostats, and appliances remotely.
-
Environmental Monitoring: Monitoring temperature, humidity, air quality, and
pollution levels.
- Smart
Agriculture: Monitoring soil moisture, temperature, and crop health in farms.
- Remote
Surveillance: Monitoring security cameras and sensors for intrusion detection.
- Industrial
Automation: Controlling and monitoring equipment and processes in factories.
- Education
and Prototyping: Learning about IoT concepts and building prototypes for
various projects.
38. Explain the importance of interfaces in IoT
devices and their role in enabling communication and interaction with other
devices or systems.
Interfaces in
IoT devices play a crucial role in enabling communication and interaction with
other devices or systems. They allow IoT devices to send and receive data,
commands, and status information, facilitating interoperability, integration,
and collaboration within IoT ecosystems. Interfaces can take various forms,
including physical interfaces (e.g., GPIO pins, USB ports), wireless interfaces
(e.g., Wi-Fi, Bluetooth, Zigbee), and software interfaces (e.g., APIs,
protocols). By providing standard interfaces and protocols, IoT devices can
communicate seamlessly with other devices, platforms, and services, enabling
interoperability, data exchange, and collaboration in IoT deployments.
39. Discuss common interfaces used in IoT devices,
such as GPIO (General Purpose Input/Output), UART, SPI, and I2C.
- GPIO
(General Purpose Input/Output): GPIO pins allow the Raspberry Pi or other
microcontroller-based devices to interact with external components such as
sensors, LEDs, and switches. They can be configured as either input or output,
allowing digital signals to be sent or received.
- UART
(Universal Asynchronous Receiver-Transmitter): UART is a serial communication
interface commonly used for asynchronous communication between
microcontrollers, sensors, and other peripheral devices. It transmits and
receives data serially, usually using two pins: one for transmission (TX) and
one for reception (RX).
- SPI (Serial
Peripheral Interface): SPI is a synchronous serial communication interface that
enables full-duplex communication between a master device (such as a
microcontroller) and one or more slave devices (such as sensors or displays).
It uses four signals: clock (SCK), master output/slave input (MOSI), master
input/slave output (MISO), and chip select (CS).
- I2C
(Inter-Integrated Circuit): I2C is a synchronous serial communication interface
commonly used for communication between integrated circuits and peripheral
devices. It uses a two-wire bus consisting of a data line (SDA) and a clock
line (SCL) to transmit data between devices.
40. Identify and describe other popular IoT devices
apart from Raspberry Pi.
Other popular
IoT devices include:
- Arduino:
Arduino boards are widely used in IoT projects due to their simplicity,
affordability, and versatility. They are based on microcontroller platforms and
can be programmed using the Arduino IDE.
-
ESP8266/ESP32: These are low-cost, low-power microcontroller modules with
built-in Wi-Fi and Bluetooth capabilities. They are commonly used for IoT
applications requiring wireless connectivity.
- BeagleBone:
BeagleBone boards are similar to Raspberry Pi but offer different features and
capabilities. They are often used in IoT projects that require higher
performance or specific I/O interfaces.
- Particle
Photon/Electron: Particle devices are IoT development kits with built-in cloud
connectivity. They are designed for easy prototyping and deployment of IoT
solutions.
- Intel
Edison/NUC: These are compact computing platforms designed for IoT and embedded
applications. They offer powerful processing capabilities and various
connectivity options.
41. Discuss the unique features and applications of
each device in the IoT ecosystem.
- Arduino:
Arduino boards are known for their simplicity and ease of use, making them
suitable for beginners and rapid prototyping. They are commonly used in
projects involving sensors, actuators, and simple control applications.
-
ESP8266/ESP32: These modules are popular for IoT projects requiring Wi-Fi or
Bluetooth connectivity. They are commonly used in home automation, smart
devices, and IoT sensor nodes.
- BeagleBone:
BeagleBone boards offer more advanced features and capabilities compared to
Arduino or Raspberry Pi, including more GPIO pins, analog inputs, and real-time
processing capabilities. They are suitable for projects requiring higher
performance or specific I/O requirements.
- Particle
Photon/Electron: Particle devices are designed for IoT applications requiring
cloud connectivity out of the box. They are commonly used in projects involving
remote monitoring, data logging, and cloud-based control.
- Intel
Edison/NUC: Intel platforms offer high performance and advanced computing
capabilities, making them suitable for IoT projects involving edge computing,
machine learning, and real-time analytics.
42. What is WAMP, and how does it facilitate
communication between IoT devices and web applications?
WAMP (Web
Application Messaging Protocol) is a protocol that enables real-time
communication between IoT devices and web applications. It is based on
WebSocket technology and provides bidirectional communication channels for
publishing and subscribing to data streams. WAMP facilitates communication
between IoT devices and web applications by allowing them to exchange messages,
events, and data in real-time, enabling interactive and responsive user
experiences.
43. Explain the key components of the WAMP protocol
stack and their functionalities.
The key
components of the WAMP protocol stack include:
- WebSocket:
WebSocket is a communication protocol that provides full-duplex communication
channels over a single TCP connection. It allows for low-latency, bidirectional
communication between IoT devices and web applications.
-
Publish/Subscribe (PubSub) Messaging Pattern: WAMP supports the
publish/subscribe messaging pattern, where IoT devices can publish data to
specific topics, and web applications can subscribe to these topics to receive
updates in real-time.
- Remote
Procedure Call (RPC): WAMP enables remote procedure calls between IoT devices
and web applications, allowing devices to invoke procedures or methods exposed
by the application and receive responses asynchronously.
44. What is Django, and how is it used in IoT
development?
Django is a
high-level Python web framework that simplifies the development of web
applications by providing a clean and pragmatic design. While Django itself is
primarily used for web development, it can be integrated with IoT projects to
create web-based dashboards, control panels, or management interfaces for
monitoring and managing IoT devices and data. Django provides features such as
authentication, authorization, database management, and templates, making it
suitable for building robust and scalable IoT applications with a user-friendly
interface.
45. Discuss the features of the Django framework that make
it suitable for building IoT applications, such as its scalability and built-in
security features.
Django offers
several features that make it suitable for building IoT applications:
-
Scalability: Django provides scalability through its architecture, allowing
developers to scale applications horizontally by adding more servers or
vertically by optimizing performance. It supports caching, database sharding,
and load balancing to handle increased traffic and data volume in IoT
deployments.
- Built-in
Security Features: Django includes built-in security features such as
authentication, authorization, and protection against common web
vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site
request forgery (CSRF). It also supports HTTPS, encryption, and user session
management to secure IoT data and communication channels.
46. What is SkyNet, and what role does it play in the
IoT landscape?
SkyNet is an
open-source platform for building IoT applications and services. It provides
tools and APIs for device management, data collection, real-time processing,
and integration with cloud services. SkyNet acts as a middleware layer between
IoT devices and cloud platforms, facilitating communication, data exchange, and
control in IoT deployments.
47. Explain how SkyNet enables device-to-device
communication and integration with cloud services.
SkyNet
enables device-to-device communication through its messaging and routing
capabilities. It supports protocols like MQTT and WebSocket for real-time data
exchange between devices. SkyNet also integrates with cloud services such as
AWS IoT, Azure IoT, and Google Cloud IoT Core, allowing devices to send data to
the cloud for storage, analysis, and visualization.
48. Discuss the advantages and limitations of using
SkyNet for IoT deployments.
Advantages of
using SkyNet for IoT deployments include:
- Simplified
Development: SkyNet provides a unified platform for IoT development, reducing
the complexity of building and managing IoT applications.
-
Scalability: SkyNet can scale to accommodate large numbers of devices and data
streams, making it suitable for scalable IoT deployments.
-
Integration: SkyNet integrates with popular cloud services, databases, and
analytics platforms, enabling seamless integration with existing
infrastructure.
-
Flexibility: SkyNet supports multiple protocols, APIs, and programming
languages, allowing developers to choose the tools and technologies that best
fit their needs.
Limitations
of SkyNet for IoT deployments may include:
- Learning
Curve: Developers may need to learn new concepts and APIs specific to SkyNet,
which could require time and resources.
- Dependency
on External Services: SkyNet relies on external cloud services for data
storage, processing, and analytics, which may introduce dependencies and
potential points of failure.
-
Customization: While SkyNet offers pre-built components and APIs for common IoT
tasks, customization may be required to meet specific project requirements or
integration needs.
49. How can IoT devices be integrated with WAMP and
Django to create scalable and interactive IoT applications?
IoT devices
can be integrated with WAMP and Django as follows:
- WAMP
Integration: IoT devices can use WAMP for real-time communication with web
applications and other devices. They can publish data to WAMP topics and
subscribe to topics to receive commands or updates.
- Django
Integration: Django can be used to build web-based interfaces, APIs, and
management tools for IoT applications. It provides features such as
authentication, authorization, and database management to create scalable and
interactive IoT applications.
50. Discuss the development process and best practices
for leveraging WAMP and Django in IoT projects.
The
development process for leveraging WAMP and Django in IoT projects involves:
- Requirement
Analysis: Understand the project requirements, including data sources,
communication protocols, user interfaces, and integration points.
-
Architecture Design: Design the architecture of the IoT system, including
components, communication channels, data flows, and security mechanisms.
-
Implementation: Develop the IoT device firmware or software using appropriate
programming languages, libraries, and frameworks. Integrate WAMP and Django
components as needed for real-time communication and web-based interfaces.
- Testing and
Validation: Conduct thorough testing of the IoT system, including functional
testing, integration testing, and performance testing, to ensure reliability,
scalability, and security.
- Deployment
and Monitoring: Deploy the IoT system in production environments and monitor
its performance, availability, and security. Implement monitoring and alerting
mechanisms to detect and respond to issues promptly.
- Continuous
Improvement: Iterate the IoT system based on user feedback, performance
metrics, and evolving requirements. Continuously improve and optimize the
system to enhance functionality, scalability, and usability over time.
51. What is Apache Hadoop, and what problem does it
solve in the context of big data?
Apache Hadoop
is an open-source framework designed for distributed storage and processing of
large datasets across clusters of commodity hardware. It solves the problem of
storing and analyzing massive amounts of data that exceed the capacity of
traditional database systems. Hadoop enables organizations to store, process,
and analyze big data in a cost-effective and scalable manner.
52. Describe the core components of Hadoop, such as
Hadoop Distributed File System (HDFS) and MapReduce.
- Hadoop
Distributed File System (HDFS): HDFS is a distributed file system that provides
high-throughput access to data across Hadoop clusters. It stores large files by
dividing them into blocks and replicating them across multiple nodes in the
cluster for fault tolerance.
- MapReduce:
MapReduce is a programming model and processing engine for parallel and
distributed processing of large datasets. It consists of two main phases: the
Map phase, where data is filtered, transformed, and grouped, and the Reduce
phase, where aggregated results are computed.
53. Explain the MapReduce programming model and its
key phases.
The MapReduce
programming model involves two key phases:
- Map Phase:
In this phase, input data is processed and transformed into intermediate
key-value pairs by applying a user-defined map function. Each mapper processes
a subset of the input data in parallel.
- Reduce
Phase: In this phase, intermediate key-value pairs with the same key are
grouped together, and the reduce function is applied to each group to produce
the final output.
54. How does MapReduce enable parallel processing of
large datasets across distributed computing clusters?
MapReduce
enables parallel processing by dividing input data into smaller chunks and
distributing them across multiple nodes in the Hadoop cluster. Each node
independently processes its portion of the data in parallel, and intermediate
results are combined to produce the final output. This parallel processing
approach allows MapReduce to scale efficiently with the size of the dataset and
the number of nodes in the cluster.
55. What is Hadoop YARN, and what role does it play in
the Hadoop ecosystem?
Hadoop YARN
(Yet Another Resource Negotiator) is a resource management and job scheduling
framework in Hadoop. It separates the resource management and processing
components of Hadoop, allowing multiple data processing frameworks to run
concurrently on a shared cluster. YARN schedules resources (CPU, memory) and
manages job execution across the cluster, enabling efficient utilization of
cluster resources.
56. Discuss the advantages of YARN over the
traditional MapReduce framework for resource management and job scheduling.
Advantages of
YARN over the traditional MapReduce framework include:
-
Flexibility: YARN supports multiple data processing frameworks (e.g.,
MapReduce, Apache Spark, Apache Flink), allowing users to choose the best tool
for their specific workload requirements.
- Resource
Sharing: YARN enables efficient resource sharing and multi-tenancy by
dynamically allocating resources based on application needs, improving cluster
utilization and performance.
-
Scalability: YARN provides better scalability than the traditional MapReduce
framework by decoupling resource management from job execution, allowing
clusters to scale to thousands of nodes.
57. What is Apache Oozie, and how does it facilitate
workflow management in Hadoop?
Apache Oozie
is a workflow scheduler system for managing Hadoop jobs. It allows users to
define, schedule, and execute complex workflows consisting of multiple Hadoop
jobs, MapReduce jobs, Pig scripts, Hive queries, and more. Oozie provides a
centralized platform for workflow management, monitoring, and coordination in
Hadoop environments.
58. Describe the key features and components of Oozie
for defining, scheduling, and coordinating Hadoop jobs.
Key features
and components of Oozie include:
- Workflow
Definition Language: Oozie uses XML-based workflow definition language to
define workflows consisting of sequential or parallel actions, dependencies,
and control flow logic.
-
Coordinator: Oozie's coordinator module allows users to define and schedule
recurring or data-driven workflows based on time or data availability triggers.
- Workflow
Scheduler: Oozie schedules and executes workflows based on defined schedules or
triggers, coordinating the execution of individual actions and managing
dependencies between them.
- Web
Console: Oozie provides a web-based user interface for managing workflows,
monitoring job status, viewing logs, and troubleshooting issues.
59. What is Apache Spark, and how does it differ from
Hadoop MapReduce?
Apache Spark
is an open-source distributed computing framework designed for large-scale data
processing. Unlike Hadoop MapReduce, which relies on disk-based processing,
Spark performs in-memory processing, making it significantly faster for
iterative algorithms and interactive analytics. Spark also offers a wider range
of APIs and supports multiple programming languages, including Java, Scala,
Python, and R.
60. Discuss the advantages of Spark in terms of
in-memory processing, iterative algorithms, and real-time analytics.
- In-Memory
Processing: Spark performs computations in-memory, reducing the need for disk
I/O and improving processing speed.
- Iterative
Algorithms: Spark's ability to cache data in memory allows for efficient
execution of iterative algorithms, making it suitable for machine learning and
graph processing tasks.
- Real-time
Analytics: Spark Streaming module enables real-time processing of streaming
data, allowing for low-latency analytics and interactive applications.
61. What is Apache Storm, and how does it address
real-time stream processing requirements?
Apache Storm
is an open-source distributed stream processing framework designed for
real-time data processing. It addresses real-time stream processing
requirements by providing fault tolerance, scalability, and low-latency
processing of continuous data streams. Storm processes data in near real-time,
making it suitable for applications such as real-time analytics, event
processing, and stream processing pipelines.
62. Explain the architecture of Apache Storm and its
integration with other big data technologies.
Apache Storm
follows a master-worker architecture where a cluster consists of a Nimbus node
(master) and multiple Supervisor nodes (workers). The Nimbus node distributes
processing tasks and monitors the cluster, while Supervisor nodes execute
processing tasks on worker machines. Storm integrates with other big data
technologies such as Apache Kafka, Apache HBase, and Apache Cassandra for data
ingestion, storage, and integration.
63. Compare and contrast Hadoop MapReduce, Apache
Spark, and Apache Storm in terms of performance, scalability, and use cases.
-
Performance: Spark generally offers better performance than MapReduce due to
in-memory processing, while Storm provides low-latency processing for real-time
data. However, MapReduce is suitable for batch processing of large datasets.
-
Scalability: All three frameworks are designed to scale horizontally across
clusters, but Spark and Storm are more suitable for real-time and iterative
processing, respectively.
- Use Cases:
MapReduce is commonly used for batch processing, ETL (Extract, Transform,
Load), and data warehousing. Spark is suitable for machine learning,
interactive analytics, and stream processing. Storm is ideal for real-time
analytics, event processing, and stream processing pipelines.
64. Discuss scenarios where each of these technologies
would be the most suitable choice.
- Hadoop
MapReduce: Suitable for batch processing of large datasets, ETL, and data
warehousing.
- Apache
Spark: Ideal for iterative algorithms, machine learning, interactive analytics,
and real-time stream processing.
- Apache
Storm: Best suited for real-time analytics, event processing, and continuous
stream processing pipelines.
65. Provide examples of real-world use cases where
Apache Hadoop, MapReduce, YARN, Oozie, Spark, and Storm have been successfully
deployed.
- Hadoop:
Used by companies like Facebook and Yahoo for large-scale data processing and
analytics.
- MapReduce:
Employed by organizations like Google and Amazon for batch processing and
analytics.
- YARN:
Utilized by enterprises for resource management and job scheduling in Hadoop
clusters.
- Oozie:
Integrated into Hadoop ecosystems for workflow management and scheduling of
MapReduce jobs.
- Spark:
Adopted by companies like Netflix and Uber for machine learning, real-time
analytics, and interactive data processing.
- Storm:
Used by companies such as Twitter and Spotify for real-time stream processing
and event-driven applications.
66. How do these technologies empower organizations to
derive insights from large volumes of data efficiently?
These
technologies empower organizations by providing scalable, distributed computing
frameworks for processing and analyzing large volumes of data efficiently. By
enabling batch processing, real-time analytics, and iterative algorithms, these
technologies allow organizations to derive valuable insights, make data-driven
decisions, and gain a competitive edge in today's data-driven world.
68. Compare and contrast Chef and Puppet as
configuration management tools. What are their primary functionalities, and how
do they facilitate automation in IoT deployments?
- Chef and
Puppet are both configuration management tools that automate the deployment,
configuration, and management of infrastructure and applications.
- Primary
functionalities:
- Chef:
Chef uses a declarative approach, where users define the desired state of the
system using code written in Ruby. It utilizes a client-server architecture
with a master server (Chef Server) and client nodes (Chef Clients) that pull
configurations from the server.
- Puppet:
Puppet follows a declarative model as well, using a domain-specific language
(DSL) to define system configurations. It operates in a client-server
architecture similar to Chef.
- Automation
in IoT deployments: Both Chef and Puppet facilitate automation in IoT
deployments by allowing developers to define and manage configurations for IoT
devices, gateways, and servers. They ensure consistency, reliability, and
scalability in IoT infrastructure management.
69. Explain the concept of infrastructure as code
(IaC) and how Chef and Puppet contribute to it in the context of IoT systems.
-
Infrastructure as code (IaC) is the practice of managing and provisioning
infrastructure using code and automation tools.
- Chef and
Puppet contribute to IaC by allowing developers to define infrastructure
configurations as code, which can be version-controlled, tested, and deployed
programmatically. This enables consistent and repeatable deployments of IoT
systems and accelerates the provisioning and management of IoT infrastructure.
70. Discuss the advantages and limitations of using
Chef and Puppet for managing IoT infrastructure and applications.
- Advantages:
-
Automation: Chef and Puppet automate the provisioning, configuration, and
management of IoT infrastructure, reducing manual effort and errors.
-
Scalability: They can scale to manage large-scale IoT deployments with
thousands of devices and servers.
-
Consistency: Chef and Puppet ensure consistency in configurations across IoT
devices and systems, improving reliability and security.
-
Limitations:
- Learning
Curve: Chef and Puppet have a steep learning curve, requiring developers to
learn their respective DSLs and architectures.
-
Complexity: Managing complex IoT deployments with diverse hardware and software
configurations can be challenging and may require advanced configuration
management strategies.
- Overhead:
Implementing and maintaining Chef and Puppet infrastructure may introduce
additional overhead and resource requirements.
71. What is NETCONF-YANG, and how does it support
network configuration and management in IoT environments?
- NETCONF
(Network Configuration Protocol) is a standardized network management protocol
defined by the IETF (Internet Engineering Task Force).
- YANG (Yet
Another Next Generation) is a data modeling language used to define the
structure and semantics of configuration and operational data.
-
NETCONF-YANG combines these two technologies to enable programmatic
configuration and management of network devices in IoT environments.
72. Describe the key components of NETCONF-YANG and
their roles in defining data models and configuring network devices.
- Key
components:
- NETCONF:
Provides a secure, XML-based protocol for remote configuration and management
of network devices.
- YANG:
Defines data models that describe the structure, hierarchy, and semantics of
configuration and operational data for network devices.
- Together,
NETCONF and YANG allow IoT devices to expose their configuration and
operational data as standardized, machine-readable models, enabling consistent
and interoperable management across heterogeneous devices.
73. How does NETCONF-YANG address the challenges
associated with managing heterogeneous IoT devices and protocols?
-
NETCONF-YANG provides a standardized approach to configuration and management,
regardless of the underlying hardware or protocol used by IoT devices.
- By defining
data models using YANG, NETCONF-YANG abstracts the complexity of individual
devices and protocols, making it easier to develop management applications and
automate configuration tasks across heterogeneous IoT environments.
74. Explain the concept of an IoT code generator and
its role in accelerating the development of IoT applications.
- An IoT code
generator is a tool or framework that automates the generation of code for IoT
applications, including device firmware, server-side logic, and management
interfaces.
- It
accelerates the development process by providing templates, libraries, and
scaffolding for common IoT tasks, reducing the need for manual coding and
speeding up time-to-market for IoT solutions.
75. Discuss the features and capabilities that
developers can expect from an IoT code generator.
-
Template-based Code Generation: Generates code based on predefined templates
and configurations for common IoT use cases and platforms.
-
Cross-platform Compatibility: Supports multiple programming languages,
frameworks, and hardware platforms commonly used in IoT development.
- Integration
with IoT Ecosystem: Integrates with other IoT tools and platforms, such as
cloud services, device management systems, and communication protocols.
-
Customization and Extensibility: Allows developers to customize generated code
and extend functionality as needed to meet specific project requirements.
- Code
Quality and Best Practices: Generates code that adheres to coding standards,
best practices, and security guidelines for IoT development.
- Continuous
Updates and Maintenance: Provides ongoing support, updates, and maintenance to
keep generated code up-to-date with evolving IoT technologies and standards.
76. How does an IoT code generator streamline the
process of integrating sensors, actuators, and communication protocols in IoT
projects?
- An IoT code
generator simplifies the integration of sensors, actuators, and communication
protocols by providing pre-built templates, libraries, and code snippets
tailored to common IoT use cases.
- It
abstracts the complexities of hardware interaction and communication protocols,
allowing developers to focus on application logic rather than low-level device
management.
- By
automatically generating code for sensor and actuator interfaces, as well as
communication protocols, an IoT code generator accelerates development and
ensures consistency across IoT projects.
77. How can tools like Chef, Puppet, NETCONF-YANG, and
IoT code generators be integrated to streamline the development and management
of IoT solutions?
- Chef and
Puppet: Used for configuration management and automation of IoT infrastructure,
ensuring consistent deployment and management of devices and applications.
-
NETCONF-YANG: Enables programmatic configuration and management of network
devices in IoT deployments, ensuring interoperability and standardization.
- IoT code
generators: Accelerate development by automating the generation of device
firmware, server-side logic, and management interfaces, reducing time-to-market
for IoT solutions.
78. Provide examples of workflows or scenarios where
these tools complement each other in IoT projects.
-
Chef/Puppet + NETCONF-YANG: Chef or Puppet can be used to automate the
deployment and configuration of IoT devices, while NETCONF-YANG facilitates
standardized management of network devices and protocols.
- IoT code
generator + Chef/Puppet: An IoT code generator can generate device-specific
configurations and scripts for Chef or Puppet, streamlining the integration of
devices into the infrastructure.
79. What are the best practices for selecting and
integrating tools in IoT development pipelines to ensure efficiency and
scalability?
- Evaluate
compatibility and interoperability between tools to ensure seamless
integration.
- Consider
the specific requirements and constraints of the IoT project when selecting
tools.
- Opt for
tools with strong community support, active development, and proven
scalability.
- Implement
robust testing and validation processes to verify the effectiveness and
reliability of integrated tools in IoT deployments.
80. Discuss the importance of security in IoT
development and management tools such as Chef, Puppet, NETCONF-YANG, and IoT
code generators.
- Security
is paramount in IoT deployments to protect sensitive data, prevent unauthorized
access, and mitigate potential threats.
-
Configuration management tools like Chef and Puppet can enforce security
policies and configurations across IoT devices and infrastructure.
-
NETCONF-YANG enables secure, programmatic management of network devices,
ensuring secure communication and access control.
- IoT code
generators should adhere to secure coding practices and standards to minimize
vulnerabilities in generated code.
81. How do these tools address security requirements
such as authentication, access control, and data encryption in IoT deployments?
- Chef and
Puppet support authentication and access control mechanisms to restrict access
to sensitive configurations and resources.
-
NETCONF-YANG facilitates secure communication between management systems and
network devices using SSH or TLS encryption and authentication.
- IoT code
generators can incorporate authentication protocols, access control mechanisms,
and data encryption techniques into generated code to enhance security.
82. What additional measures can developers take to
enhance the security of IoT solutions when using these tools?
- Implement
strong authentication mechanisms such as multi-factor authentication (MFA) for
device access.
- Enforce
secure communication protocols such as TLS/SSL for data transmission between
devices and servers.
- Regularly
update and patch IoT devices and management systems to address known
vulnerabilities and security issues.
- Conduct
security audits and penetration testing to identify and remediate potential
security weaknesses in IoT deployments.
83. Evaluate the scalability and performance
characteristics of Chef, Puppet, NETCONF-YANG, and IoT code generators in the
context of large-scale IoT deployments.
- Chef and
Puppet: Both are horizontally scalable and can manage large numbers of devices
and configurations efficiently. Performance depends on factors such as the size
of the infrastructure and the complexity of configurations.
-
NETCONF-YANG: Designed for scalability and can handle large-scale network
deployments with thousands of devices. Performance may vary based on network
size and traffic volume.
- IoT code
generators: Performance and scalability depend on factors such as code
complexity, generation time, and resource utilization. They should be able to
scale to meet the demands of large-scale IoT deployments.
84. Discuss strategies for optimizing the performance
and scalability of these tools to meet the requirements of IoT applications
with high data volumes and real-time processing needs.
- Utilize
distributed architectures and load-balancing techniques to distribute workload
evenly across nodes.
- Optimize
configurations and workflows to minimize overhead and maximize efficiency.
- Implement
caching mechanisms and resource pooling to reduce latency and improve
responsiveness.
- Monitor
performance metrics and conduct regular performance tuning to identify and
address bottlenecks in the system.

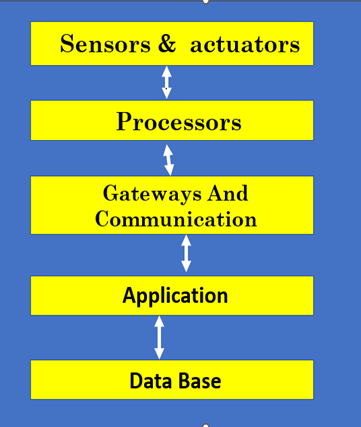
0 Comments