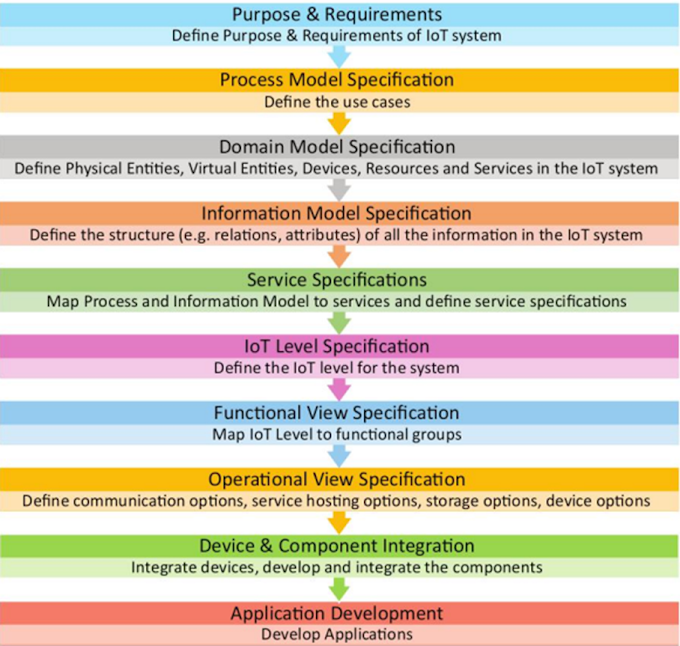
Simple Network Management Protocol (SNMP)
- SNMP is used at the application layer of the TCP/IP architecture.
- used to manage and monitor network and network faults.
- Also used to modify the configuration of the remote end devices of the network.
- The devices compatible with SNMP Protocol are modems, routers, switches, printers, servers, etc.
SNMP Components
1. SNMP Manager
- ·
It is a
centralized GUI-based node system that is used to monitor the network and is
also called a Network Management System (NMS).
- ·
A manager is a
host that runs the SNMP client program while the agent is a router that runs
the SNMP server program.
- ·
Executes
SNMP commands to monitor and configure the Managed Device.
- ·
It interfaces the
bi-directional flow of information between the NMS node and the network
elements.
- ·
Network elements
are switches, routers, servers, modems, computer hosts, IP-based phone and video
cameras, etc.
2. SNMP Agent
- ·
The agent is the
module of network management software that is installed on a
network device like a host PC, server and router, etc.
- · The agent is used to keep the information in a database while the manager is used to access the values in the database.
- ·
A server program
on the agent checks the environment, if something goes wrong, the agent sends a
warning message to the manager.
- · Agent software runs on the hardware or service being monitored, collecting data about disk space, bandwidth use, and other important network performance metrics. When queried by the SNMP manager, the agent sends the requested information back to the management system. An agent may also proactively notify the NMS if an error occurs.
- Management Information Database (MIB)
This MIB database is a text file (.mib) that itemizes and describes all objects on a particular device that can be queried or controlled using SNMP.
Each MIB item is assigned an object identifier (OID).
Store all the information of the device attributes to be managed.
Structure of MIB:
·
It is a group of
information that comprises the variables that reside in the values relevant to the
parameters of the network element in its stores. These variables are known as
managed objects and are identified by an Object Identifier (OID).
·
MIB is a
collection of object identifiers in a hierarchical format, and each can
identify a variable that can be set or read by the SNMP.
·
The OIDs are of
two kinds, scalar and tabular. The scalar one report only a single event
instance means that the result is only one.
·
The Tabular object
is a table that is a pool of all related OIDs and thus gives multiple results
for one object value.
SNMP Commands
By deploying the SNMP, the
network elements are managed by using three commands: Read, Write, and Trap.
Read command is deployed by the NMS
to monitor the managed network elements like routers, switches, etc. This
action is completed by NMS by examining the various variables that are upheld
by the network elements.
Write command is deployed by the NMS
to control the network elements. Through this command, the NMS can alter the
values of the variables which are stored in the managed network elements.
Trap command is
utilized by the managed network elements to report the incidences and errors to
the NMS.
The SNMP request messages include the
operations like ‘Get’, GetNext’, and ‘GetBulk’.
·
Get: By using this message, the NMS request to
retrieve more than one variable from the SNMP agent.
·
GetNext: This operation permits the NMS to retrieve
one or greater than one consequent variable from the SNMP agent.
·
GetBulk: This operation is correspondent to the
consecutive GetNext operation. With this set of request messages, we can
retrieve the database from the agent in bulk.
·
Response: It returns the variable data unit from the
agent to the NMS in response to the Get and Set request PDUs.
·
Trap: This command is initiated by the SNMP agents.
When an event occurs the agent sends a signal to the SNMP manager to acknowledge
the occurrence in the form of this PDU.
·
InformRequest: Its function is the same as that of the Trap
command. It includes the acknowledgment of receiving the packet from the SNMP
manager.
Limitations of
SNMP
Several
limitations are.
- ·
SNMP
is a connectionless protocol that uses UDP as the transport protocol, making
it unreliable as there was no support for acknowledgment of requests.
- ·
MIBS
often lack writable objects without which device configuration is not possible
using SNMP.
- ·
With
the absence of writable objects, SNMP can be used only for device monitoring
and status polling.
- ·
It
is difficult to differentiate between configuration and state data in mibs.
- ·
Retrieving
the current configuration from a device can be difficult with SNMP.
- ·
SNMP
does not support easy retrieval and playback of configurations.
- ·
Earlier
versions of SNMP did not have strong security features making the management. Security
features of SNMP, increased the complexity a lot.
=============================================================================


0 Comments